CDEXOS Overview: As companies rely increasingly on technology to conduct their operations and store sensitive information, cybersecurity is a critical aspect of any modern business. In order to effectively protect against cyber threats, it is essential to consider three key factors: the assets that need to be protected, the potential attackers, and the defenses that are in place. This article will explore each of these factors in depth, providing examples of how they apply to real-world companies and explaining the importance of considering each one when developing a cybersecurity strategy… Enjoy!
Your Cybersecurity Solution Starts Here!
You need to evolve your Cybersecurity protection, but where do you start? CDEXOS helps organizations identify, protect and respond to cyber threats. Our mission prioritizes business decisions so you make informed decisions on data protection, cloud migration, and cybersecurity.
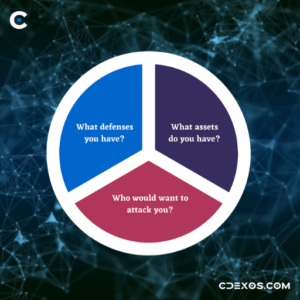
3 Key Factors of Cybersecurity Model
With the increasing amount of sensitive information being stored and shared electronically, it’s more important than ever to protect against cyber-attacks. However, understanding and implementing effective cybersecurity measures can be a daunting task. To make the process more manageable, it’s essential to break it down into its core components. One of the most important ways to do this is by focusing on three key factors: assets, attackers, and defenses.
1. Assets
Assets refer to the valuable information and resources that a company possesses and that an attacker may target. Identifying and understanding these assets is the first step in securing them from cyber-attacks. Assets can include a wide range of information and resources such as customer data, financial information, intellectual property, and confidential business information.
For example, a healthcare company would want to protect patient records and other sensitive medical information. This data can include personal information such as names, addresses, social security numbers, and medical history. A breach of this information could result in serious harm to patients, as well as potential legal and reputational damage to the healthcare company.
Similarly, a financial institution would want to protect banking and financial data. This can include information such as account numbers, balances, and transactions. A breach of this information could lead to financial loss for customers, as well as potential legal and reputational damage for the financial institution.
It is important for companies to regularly review and update their inventory of assets in order to ensure that they are aware of all the valuable information and resources they possess and that they are taking the appropriate measures to secure them. This can include implementing security measures such as encryption, access controls, and regular backups, as well as training employees on how to handle sensitive information securely.
2. Attackers
Attackers in the context of cybersecurity are individuals or groups who attempt to gain unauthorized access to a company’s assets. These attackers can range from individual hobbyist hackers, also known as “white hat” hackers, to organized criminal groups, also known as “black hat” hackers. Nation-states also can be considered as attackers.
For example, a retail company may be targeted by black hat hackers looking to steal customer data for financial gain. This data can include personal information such as names, addresses, and credit card numbers, which can be sold on the black market or used to commit fraud. The retail company may also be targeted by a nation-state looking to steal sensitive information about new technologies.
A defense contractor may also be targeted by black hat hackers or nation-states looking to steal sensitive information about new technologies. This information can include details about new weapons systems, intelligence gathering techniques, and other classified information.
It’s important for companies to understand the potential attackers and their motivations to tailor their defense mechanisms accordingly. For example, a company that is aware of a nation-state’s interest in their technologies will have to implement different security measures than a company that’s aware of a financial gain-motivated attackers.
In addition, it is also important to understand that attackers are continually evolving their tactics and that companies must regularly assess and update their threat model to stay ahead of potential threats.
3. Defenses
Defenses is one of the three key factors of cybersecurity model. It refer to the measures and technologies that a company puts in place to protect against cyber-attacks. These defenses can include a wide range of tools and strategies, such as firewalls, intrusion detection systems, encryption, and security awareness training for employees.
For example, a company might use a combination of firewalls and intrusion detection systems to block unauthorized access to its network. Firewalls act as a barrier between a company’s internal network and the internet, controlling and monitoring incoming and outgoing traffic. Intrusion detection systems monitor a company’s network for signs of unauthorized access or malicious activity. Together, these two defenses can provide a strong barrier against unauthorized access to a company’s network.
Another defense that companies can use is encryption. Encryption is the process of converting plaintext into unreadable text, which can only be read by someone who has the key to decrypt it. By encrypting sensitive information, companies can protect it from being intercepted or stolen by unauthorized parties.
Security awareness training is also an important defense against cyber-attacks. By training employees to recognize phishing emails and other tactics used by attackers, companies can reduce the risk of employees falling victim to these attacks and inadvertently giving attackers access to sensitive information. Trusted advisor can play a crucial role in this step, by providing training and guidance, and being a point of contact for employees when they suspect an attack.
CDEXOS Summary
A comprehensive cybersecurity strategy must take into account the assets that need to be protected, the potential attackers, and the defenses that are in place. Identifying and understanding the valuable assets of a company is the first step in securing them from any cyber-attacks. After identifying the assets, it is crucial to understand the type of attackers that may target the company and their motivations. Only by understanding the potential attackers, companies can tailor their defense mechanisms accordingly. The final step is to implement effective defenses such as firewalls, intrusion detection systems, encryption, and employee education and awareness programs. By taking these three key factors into account, companies can better protect themselves against cyber threats and minimize the risk of a successful attack.
Let CDEXOS provide you with a complementary Cybersecurity Assessment by completing our request form today!
Sam Palazzolo, Founder/CEO